Leveraging the Datto Networking Managed SOC integration
NAVIGATION Partner Portal > Networking Status > Network Manager > Access Points > Advanced
NAVIGATION Partner Portal > Networking Status > Network Manager > Switches > Switch settings
With Datto Networking, you have the ability to configure your switches, access points, and Secure Edge Gateways to send curated sets of syslog events to Managed Security Operations Centers (SOCs) and SIEM tools. These logs are useful for identifying potential Indicators of Compromise (IoCs) in your environment. This article describes the process to set up the integration for each of the endpoints.
NOTE This feature is available to be used with any SIEM that supports the CEF format and has built parsing rules to ingest the log messages that your devices will send. It does not enable low-level system messages.
Prerequisites 
To set up the Managed SOC integration, you'll need the following:
Environment prerequisites 
-
You must have access to the Datto network you'd like to connect to your Managed SOC.
-
A SIEM that supports the Common Event Format (CEF), configured with parsing rules, must be present to ingest the log messages that the network devices will send.
-
At least one endpoint agent in your environment needs to be capable of aggregating and sending the syslogs that you want to forward to your SIEM/Managed SOC integration.
-
Additional endpoint-specific prerequisites are listed below.

Datto Switch prerequisites
-
Switches must be Generation 2 (DSW series).
NOTE This feature is not available for Generation 1 (E/L series) switches.
-
Switches must have firmware version 1.00.19 or greater.
Procedure
-
Navigate to portal.dattobackup.com
-
Log in with your Partner Portal credentials.
-
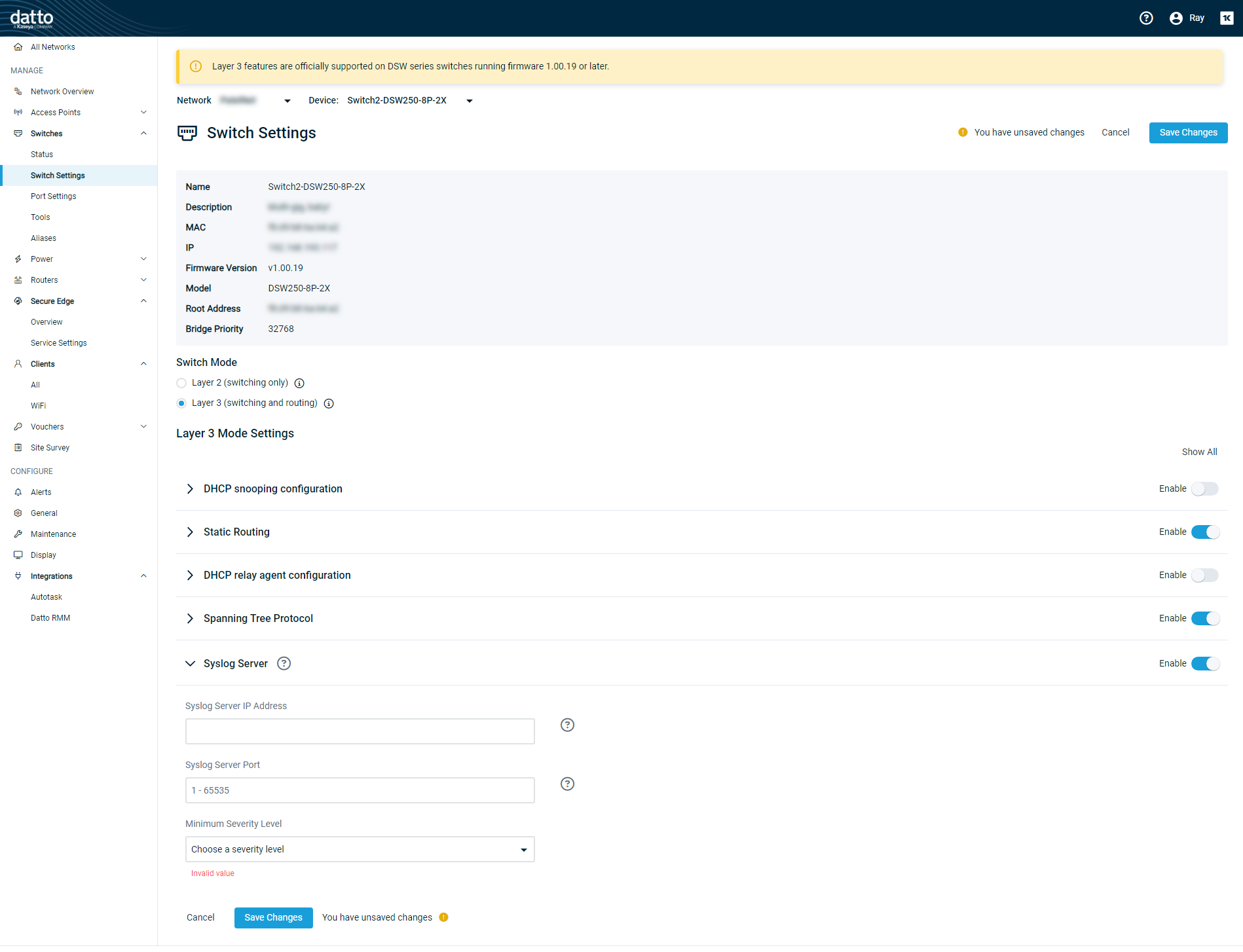
Scroll to the Syslog Server section of the Switches page.
-
In the Syslog Server IP Address field, enter the IP address of the primary receiving syslog server or SIEM tool.
-
Next, enter the UDP port number of the primary receiver in the Syslog Server Port field. The valid port range is 1-65535. Port number 514 is common.
-
Finally, in the Minimum Severity Level drop-down menu, select the severity level of the alerts you'd like to receive. The level defines the minimum severity a log message must possess to be eligible for export to the external syslog server.
-
Click Save Changes. Your Datto Switch will begin sending curated syslog events to your SOC as they occur.

Datto Access Point prerequisites
-
All Access Points on the network must be on firmware version 7.0.17 or higher.
Procedure
-
Navigate to portal.dattobackup.com
-
Log in with your Partner Portal credentials.
-
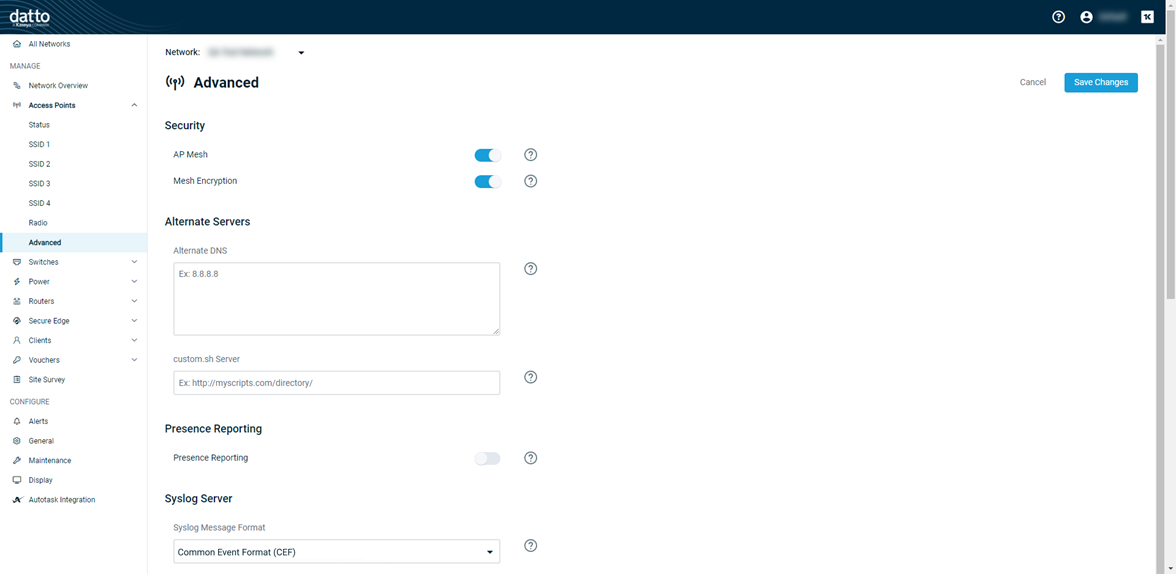
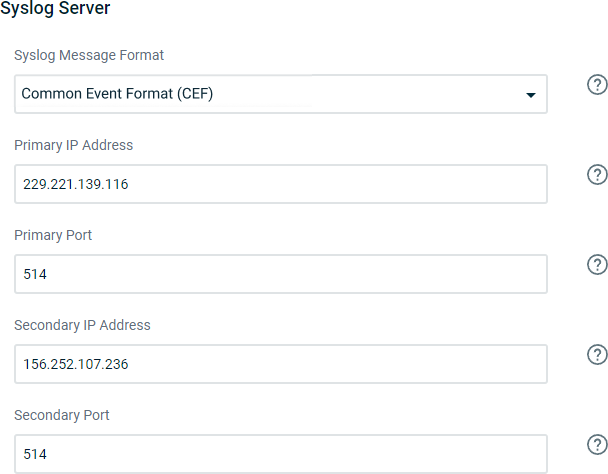
Scroll to the Syslog Server section of the Advanced page.
-
In the Primary IP Address field, enter the IP address of the primary receiving syslog server or SIEM tool.
-
Next, enter the UDP port number of the primary receiver in the Primary Port field. The valid port range is 1-65535. Port number 514 is common.
-
Then, if you have a secondary syslog receiver, enter its IP address in the Secondary IP Address field.
-
Finally, input the UDP port number of the secondary syslog receiver in the Secondary Port field.
-
Ensure that the selection in the Syslog Message Format drop-down menu is set to Common Event Format (CEF).
IMPORTANT This step is required. The legacy format is not compatible with RocketCyber and other comparable SIEM/SOC tools.
-
Click Save Changes. Your Access Points will begin sending curated syslog events to your SOC as they occur. For event definitions, refer to the next section of this article.
Understanding syslog events generated by Access Points 
The following table lists the events that Access Points (APs) may send to your syslog receiver and provides examples of each type of notification. For definitions of the extension (placeholder) values shown, refer to the Extension definitions section of this article.
Events
| Event type | Example |
|---|---|
| AP responds to a probe request | CEF:1|Datto|AccessPoint|7.1.0|wifi|probe|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR
|
| Device boot | CEF:1|Datto|AccessPoint|7.1.0|system|boot|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR
|
| Device reboot | CEF:1|Datto|AccessPoint|7.1.0|system|reboot|2|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR reason:REBOOT_REASON
|
| IP address assigned to a station by the AP | CEF:1|Datto|AccessPoint|7.1.0|dhcp|up|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR dmac:STATION_MAC_ADDR dvc:IP_ADDR dvchost:HOSTNAME cs2:SSID_NAME
|
| IP address released from a station on the AP | CEF:1|Datto|AccessPoint|7.1.0|dhcp|down|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR dmac:STATION_MAC_ADDR dvc:IP_ADDR cs2:SSID_NAME
|
| Station attempts to associate with the AP | CEF:1|Datto|AccessPoint|7.1.0|wifi|assoc|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR reason:REASON_CODE
|
| Station attempts to authenticate with the AP | CEF:1|Datto|AccessPoint|7.1.0|wifi|auth|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR reason:REASON_CODE
|
| Station attempts to re-associate with the AP | CEF:1|Datto|AccessPoint|7.1.0|wifi|reassoc|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR reason:REASON_CODE dattoDevicePreviousAP:PREVIOUS_AP_MAC_ADDR
|
| Station attempts to use the wrong WiFi password for the SSID defined in cs2; high number (40+) of attempts in tight succession could indicate password guess attempt | CEF:1|Datto|AccessPoint|7.1.0|wifi|key-mismatch|7|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR
|
| Station disassociated from the AP | CEF:1|Datto|AccessPoint|7.1.0|wifi|disassoc|0|rt=TIME_SINCE_EPOCH smac=AP_MAC_ADDR cs2:SSID_NAME dmac:STATION_MAC_ADDR reason:REASON_CODE
|
| Station unauthenticated from the AP |
|
Extension definitions
| Extension | Definition |
|---|---|
| dattoDevicePreviousAP | The MAC address of the last station to which the AP connected |
| TIME_SINCE_EPOCH | Time since the epoch, used as time when the event was received by the AP |
| AP_MAC_ADDR | The MAC address of the AP sending the event to the endpoint |
| STATION_MAC_ADDR | The MAC address of the WiFi device interacting with the AP |
| IP_ADDR | IP address of WiFi device interacting with the AP |
| HOSTNAME | Hostname of the WiFi device interacting with the AP |
| REBOOT_REASON | Reason for the device reboot; usually initiated by the cloud. |
| SSID_NAME | The WiFi SSID the device is interacting with. EG: 'Starbucks WiFi' |
| REASON_CODE | The IEEE 802.11 reason code given to the WiFi device interacting with the AP |

Secure Edge Gateway prerequisites
-
You must have at least one registered and active Gateway for these configuration options to be available.
Procedure
-
Navigate to portal.dattobackup.com
-
Log in with your Partner Portal credentials.
-
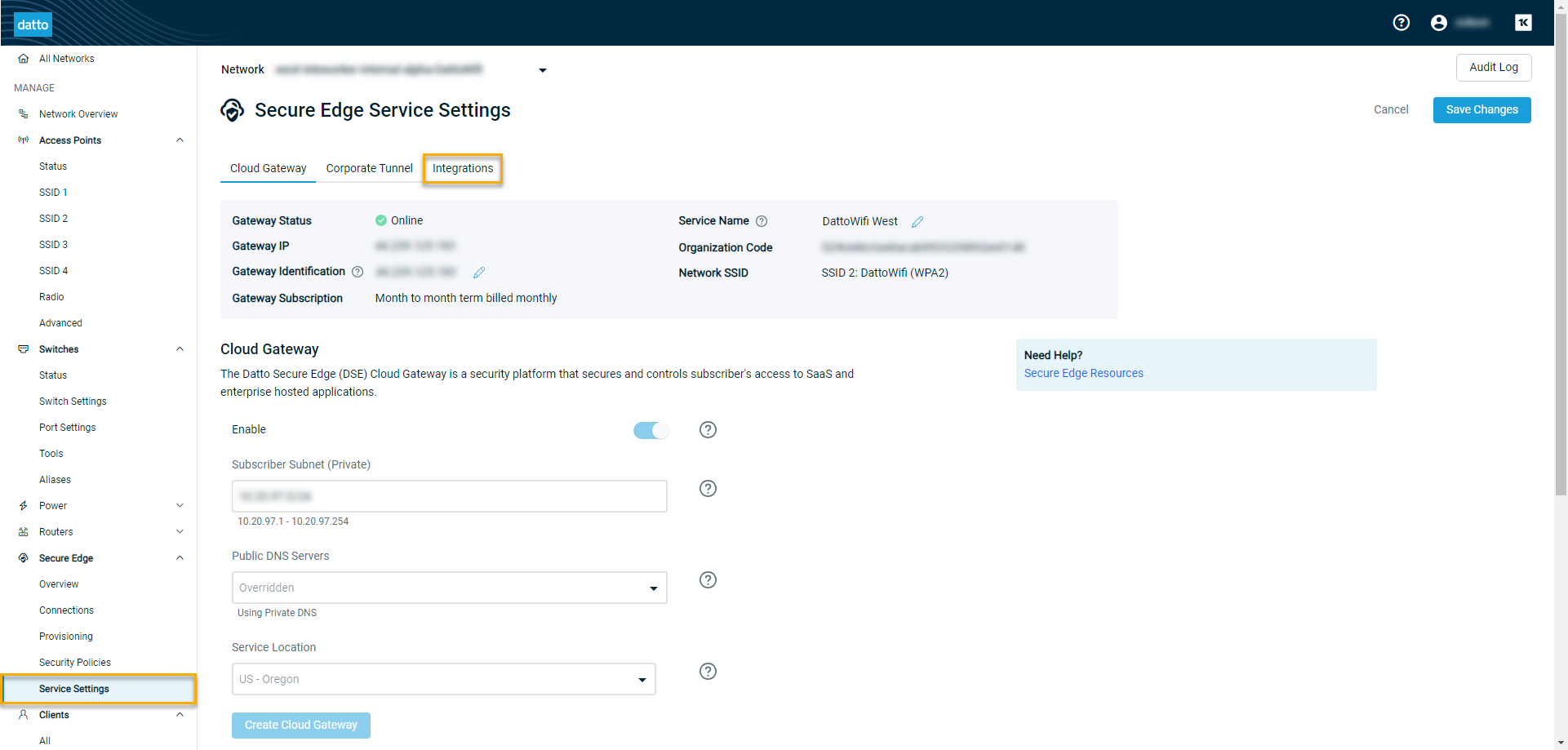
In the left navigation menu, expand the Secure Edge category.
-
Click Service Settings.
-
On the Secure Edge Service Settings page, select the Integrations tab.
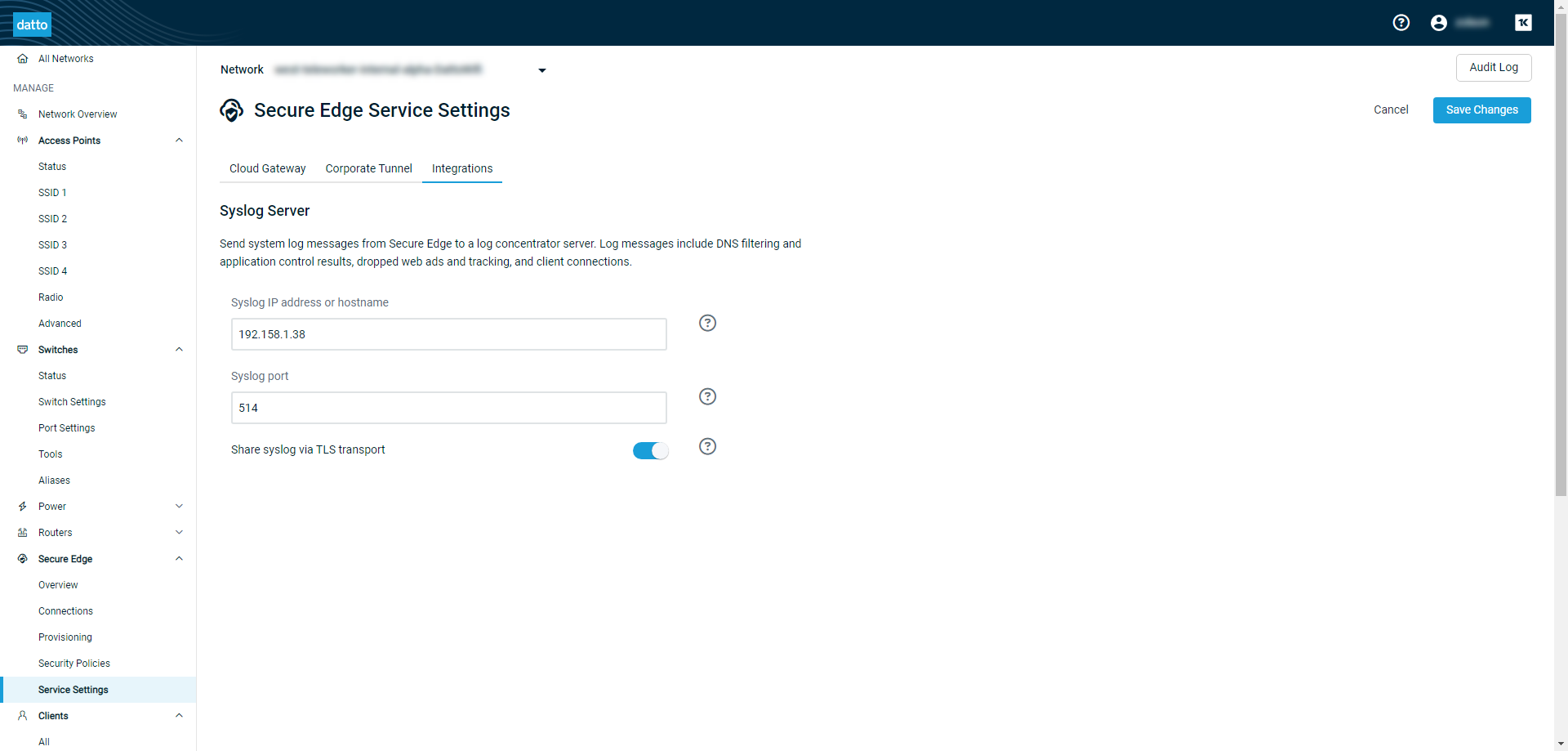
-
In the Syslog IP address or hostname field, enter the IP address or hostname of the primary receiving syslog server or SIEM tool. For example, you can input 192.158.1.38 or www.example.com.
-
Next, enter the UDP port number of the primary receiver in the Syslog port field. The valid port range is 1-65535. Port number 514 is common.
-
If you'd like to use Transport Layer Security (TLS) to encrypt the Secure Edge data sent to the syslog server, turn on the Share syslog via TLS transport toggle.
-
Click Save Changes. Your Secure Edge Gateway will begin sending curated syslog events to your SOC as they occur.
Understanding syslog events generated by Secure Edge 
The following table lists the events that Secure Edge may send to your syslog receiver and provides examples of each type of notification.
| Event type | Example |
|---|---|
| APP-Control traffic drop | CEF:1|Datto|Secure Edge|1.2.1|traffigatord|drop|7|groups.0=soundcloud client_ip=CLIENT_IP event_time=APP_CONTROL_DROP_TIMESTAMP action=drop external_type=software identification_code=ORGANIZATION_CODE subscriber=SUBSCRIBER_EMAIL peer_id=SOFTCLIENT_OR_APPLIANCE_ID user_id=SUBSCRIBER_ID event_type=EVENT_TYPE trigger=EVENT_TRIGGER policy_id=SECURITY_POLICY_IDexternal_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR
|
| Client connected |
CEF:1|Datto|Secure Edge|1.2.1|instance-agent|connected|3|cloud_ip=CLIENT_CLOUD_IP_ADDR service_instance_id=SERVICE_INSTANCE_ID client_event=connected peer_id=SOFTCLIENT_OR_APPLIANCE_ID identification_code=ORGANIZATION_CODE wan_ip=CLIENT_WAN_IP network_id=SUBSCRIBER_NETWORK_ID subscriber=SUBSCRIBER_EMAIL external_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR duration=0 timestamp=EVENT_GENERATE_TIMESTAMP
|
| Client disconnected | CEF:1|Datto|Secure Edge|1.2.1|instance-agent|disconnected|3|subscriber=SUBSCRIBER_EMAIL service_instance_id=SERVICE_INSTANCE_ID client_event=disconnected external_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR cloud_ip=CLIENT_CLOUD_IP_ADDR duration=CLIENT_DISCONNECTED_TIMESTAMP identification_code=ORGANIZATION_CODE peer_id=SOFTCLIENT_OR_APPLIANCE_ID network_id=SUBSCRIBER_NETWORK_ID timestamp=EVENT_GENERATE_TIMESTAMP wan_ip=CLIENT_WAN_IP
|
| DNS filtering allow | CEF:1|Datto|Secure Edge|1.2.1|coredns|allow|1|identification_code=ORGANIZATION_CODE subscriber=SUBSCRIBER_EMAIL socket_family=DNS_REQUEST_PROTOCOL domain=REQUEST_DOMAIN external_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR client_ip=CLIENT_CLOUD_IP_ADDR action=allow response_time=DNS_RESPONSE_TIMESTAMP policy_id=SECURITY_POLICY_ID user_id=SUBSCRIBER_ID external_type=software query_time=DNS_QUERY_TIMESTAMP socket_protocol=DNS_REQUEST_PROTOCOL src_addr=CLIENT_CLOUD_IP & SOURCE_PORT peer_id=SOFTCLIENT_OR_APPLIANCE_ID
|
| DNS filtering drop | CEF:1|Datto|Secure Edge|1.2.1|coredns|drop|7|action=drop policy_id=SECURITY_POLICY_ID peer_id=SOFTCLIENT_OR_APPLIANCE_ID client_ip=CLIENT_CLOUD_IP_ADDR identification_code=ORGANIZATION_CODE subscriber=SUBSCRIBER_EMAIL response_time=DNS_RESPONSE_TIMESTAMP src_addr=CLIENT_CLOUD_IP_ADDR_AND_SOURCE_PORT groups.0=ads groups.1=basic groups.2=crypto external_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR external_type=SOFTAWRE_DOMAIN query_time=DNS_QUERY_TIMESTAMP user_id=SUBSCRIBER_ID socket_family=INET socket_protocol=DNS_REQUEST_PROTOCOL
|
| Traffic generate | CEF:1|Datto|Secure Edge|1.2.1|telemeterd|TRAFFIC_CLASSIFICATION|3|client_ip=CLIENT_CLOUD_IP_ADDR port_dst=DESTINATION_PORT identification_code=ORGANIZATION_CODE peer_id=SOFTCLIENT_OR_APPLIANCE_ID subscriber=SUBSCRIBER_EMAIL external_id=SOFTCLIENT_UUID_OR_APPLIANCE_MAC_ADDR priority=TRAFFIC_PRIORITY proto=APPLICATION_PROTOCOL agg_ts=AGGREGATION_TIMESTAMP external_type=SOFTWARE/APPLIANCE user_id=SUBSCRIBER_ID port_src=CLIENT_SOURCE_PORT class=TRAFFIC_CLASSIFICATION flow_type=UL_UPLOAD_OR_DL_DOWNLOAD packets=AGGREGATED_PACKET_COUNT ip_proto=TRANSPORT_PROTOCOL policy_id=SECURITY_POLICY_ID resource_ip=DESTINATION_IP_ADDR
|