Outbound NAT
This article describes the Outbound NAT feature for the Datto Networking Appliance (DNA).
Environment 
- Datto Networking Appliance (DNA)
Description 
The Outbound NAT feature allows an operator to configure firewall rules which route traffic through alternate source IP addresses in the private subnets. This feature requires more than one static IP and permits you to specify which external IP address to use for a given host (one IP) or subnet.
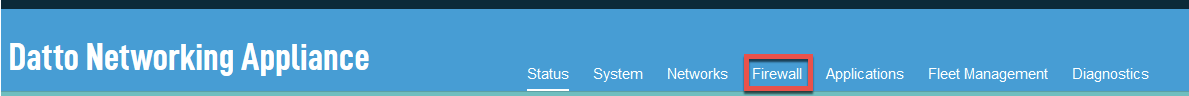
To access the Outbound NAT card, log into the DNA web interface, and click Firewall, as shown in Figure 1.
Once on the Firewall page, click the Outbound NAT link. You will see the Outbound NAT management card shown in Figure 2.
To create a new Outbound NAT rule, select the Egress IP address you want the rule to apply to. Click New Rule, and configure the following settings:
- Enabled: Check the box if you want this rule to be enabled on save. Uncheck the box to create the rule, but not enable it.
- Name: Specify the name of the rule. Use a name that will remind you what the rule does.
- Type: Select the source type.
- If the Type is Host, the source is a valid internal IP address
- If the Type is Network, the source is a valid internal IP address and netmask in CIDR form (for example 192.168.1.1/24)
- Source: Enter the source IP address that you want to route through the selected Egress IP.
Once you have finished configuring the rule, click Save Changes.
Example Use Case 
An MSP has three static IP addresses: 7.7.7.7, 7.7.7.8, and 7.7.7.9.
LAN traffic to the Internet goes out of the primary / main IP of 7.7.7.7 by default. The local address for the LAN is 192.168.111.1/24.
On the same LAN, the MSP has an Exchange server that they want to use a different egress IP for.
So they add an egress rule for 7.7.7.8, with the local address of the server 192.168.111.50.
The MSP also decides that they want another LAN to go out of a third IP. They add another egress rule for 7.7.7.9 with the address of that LAN :192.168.222.1/24