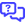Datto Secure Edge Firewall Rules
The Secure Edge product is a cloud firewall and sometimes it is necessary to filter using IP addresses, IP protocols and IP ports. Secure Edge already has the capability to filter DNS queries and filter applications using application control. Sometimes DNS filtering and application control filtering is not enough.
With Zero Trust Network Access (ZTNA) you want to only allow very restricted access to specific resources. With port, protocol and Address firewall rules you would provide very limited access to one application located on a server behind a firewall.
Environment
- Datto Secure Edge
Description
Firewall Rules are essential part of an Seurity Policy for Secure Edge Subscribers. They can be used to block access to sensitive resources by using a set of filters that block ports, protocols and destination IP addresses. It’s important to configure these rules to deny access to applications and resources that are not allowed by this user or group of users.
Firewall rules are defined from the perspective of the ingress (inbound side) of the cloud firewall and are processed in priority sequence (starting with priority 1, going downwards). The first policy that applies to the packet is applied.
Navigating to Security Policy Settings
-
In Datto Network Manager, click Secure Edge in the Navigation menu, then select Security Policies from the expanded options.
-
On the Security Policies page, click the name of the policy you'd like to modify.
-
Click Firewall to continue.
Adding a new rule
-
Select Add Firewall Policy, to create a new firewall rule.
-
Fill out each of the fields by entering the value or selecting it from the provided dropdowns.
-
Firewall Rule Name: Enter a name to easily identify the rule being created.
-
Status: Set the status to Active if you would like the rule applied, or Inactive to currently disable the rule.
-
Action: Select to allow or block traffic with the policy, from the dropdown.
-
Protocol: Select the protocol from the dropdown from Any, TCP, or UDP.
-
Source Port: Enter a single port, range of ports, or "Any" to allow/block all traffic for the destination IP(s).
-
Destination IP: Select the formatting of the destination addresses from either:
- All, to make the policy not dependent on the destination address.
- Address, to input a single IP address.
- Subnet, to input a range of addresses using CIDR notation: 10.48.50.0/24
- Range, to input a range of addresses using a dash: 10.13.5.6-10.13.5.11
-
Destination Address(es): Enter the IP address of the of the destination, matching the formatting to the Destination IP type selected.
-
Destination Port: Enter a single port, range of ports, or "Any" to allow/block all traffic for the destination IP(s).
-
-
Select the check mark to save the new policy, or the x icon to remove it. Saved policies can later be changed with the three dot menu on the right side of the policy.
-
Once created the rule's priority can be changed by reordering the current rules in the list. Click and hold the icon on the left of the priority number to drag it up or down. The rules are evaluated in ascending numerical order of priority and the first matching policy is used.