Setting up the Corporate Tunnel for use with Sophos firewalls
NAVIGATION Partner Portal > Networking Status > Network Manager > Manage > Secure Edge > Service Settings > Subscriber Settings
PERMISSIONS Access to manage your Sophos firewall's configuration
This article explains how to set up the Corporate Tunnel through Sophos firewalls for use by your Secure Edge clients.
Procedure 
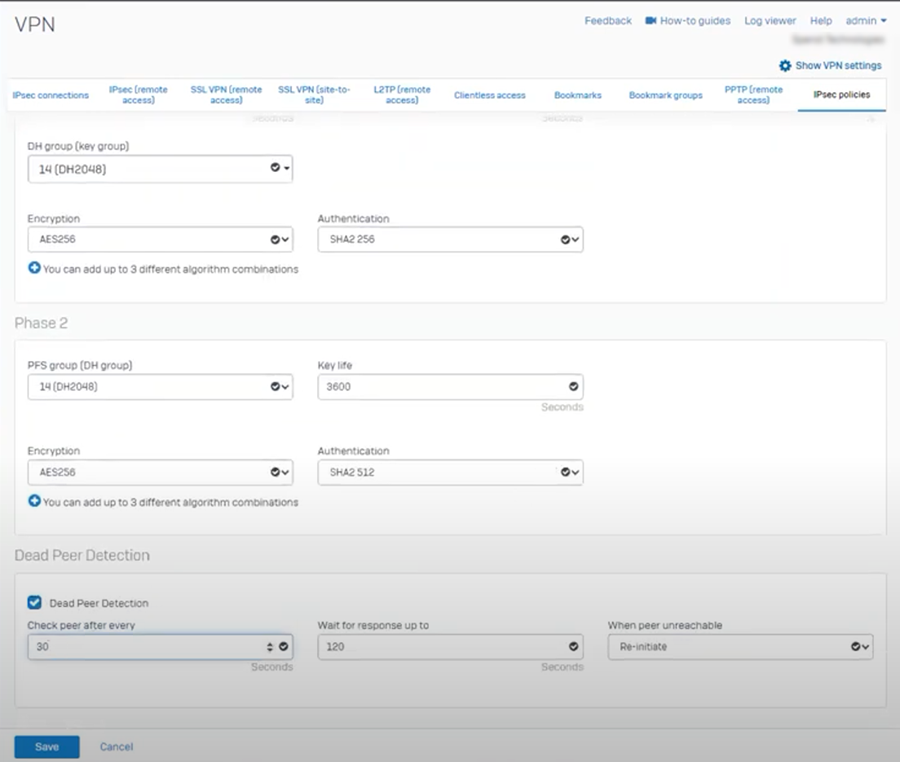
Sophos configuration 
BEFORE YOU BEGIN The Secure Edge Cloud Gateway is always the VPN server (receiver), so the Sophos firewall and any other endpoint must be configured as the VPN initiator.
-
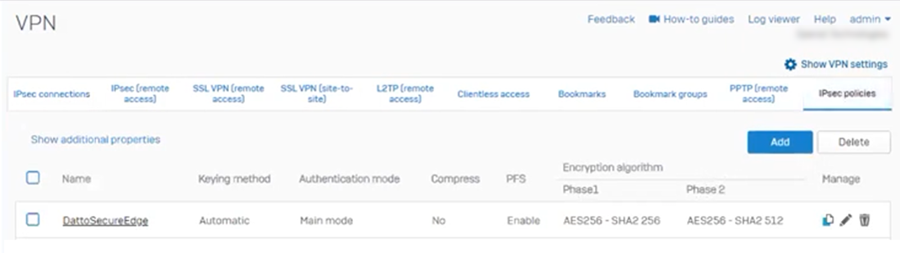
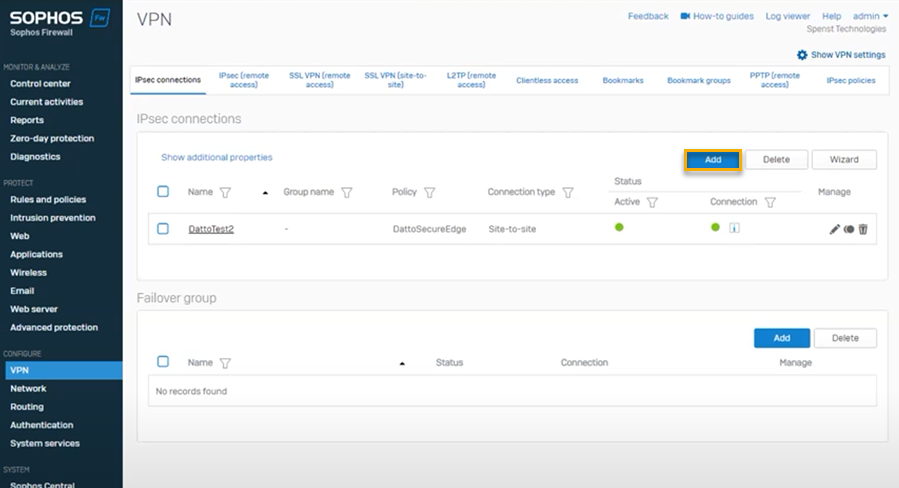
Open your Sophos Firewall console and navigate to Configure > VPN.
-
In the IPsec connections section of the page, click Add.
NOTE If you prefer to add an IPsec connection by using the wizard, you can click the Wizard button instead. When prompted, enter the settings described in the following steps.
-
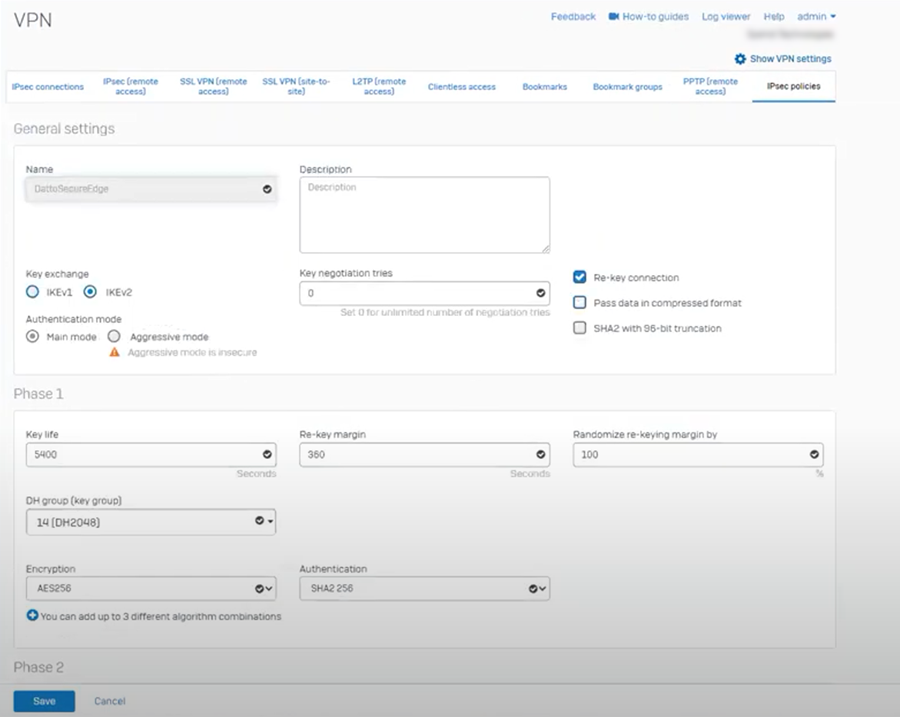
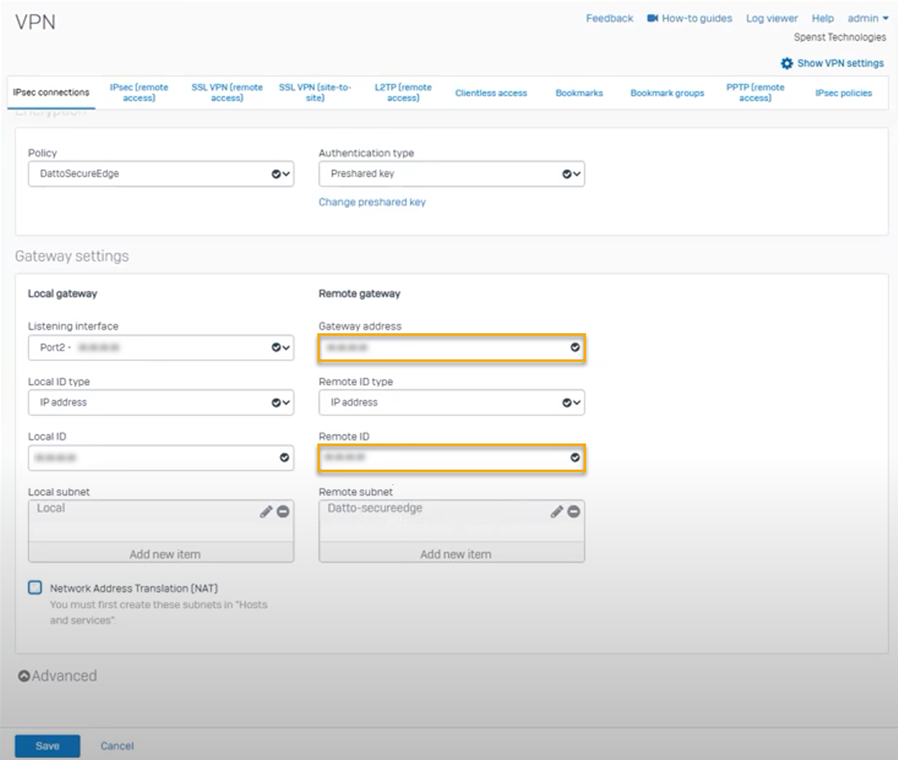
On the IPsec connections tab, in the Gateway settings section of the page, input the gateway IP of the Secure Edge appliance in the Remote gateway > Gateway address field.
-
Set the Remote ID drop-down to IP address and enter the gateway IP of the Secure Edge appliance in the Remote gateway > Remote ID field.
-
Complete any other required fields. Then, click Save.
Secure Edge configuration 
-
Navigate to portal.dattobackup.com
-
Log in with your Partner Portal credentials.
-
From the left navigation menu, select Secure Edge to expand the options available.
-
From the left navigation menu, select Service Settings.
-
The Service Settings page loads.
-
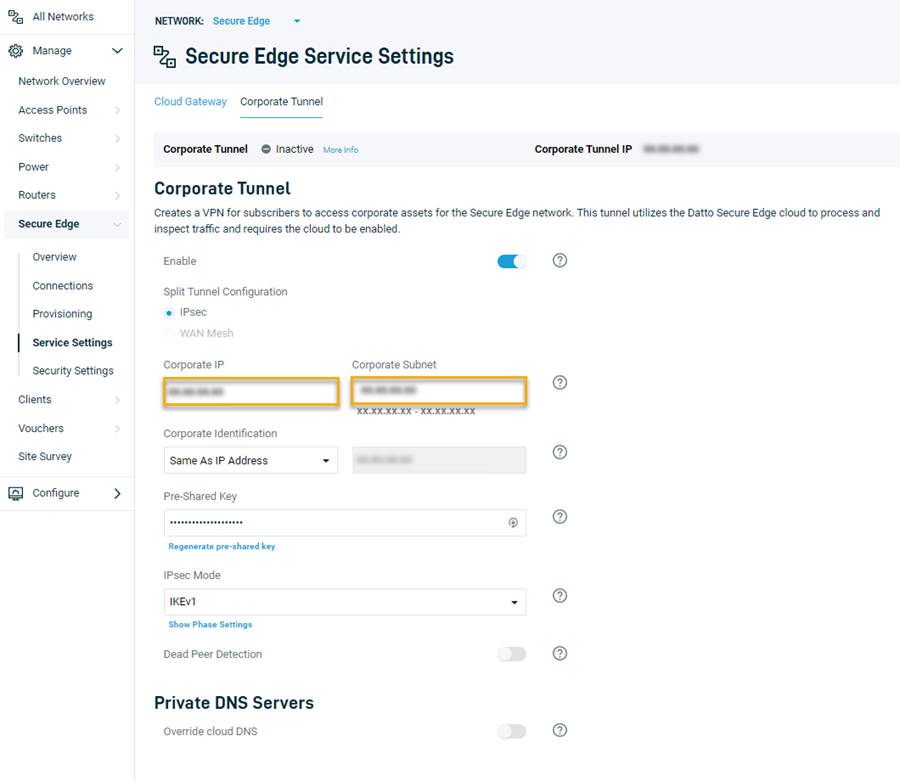
Access your Corporate Tunnel settings.
-
Enter the Sophos Listening interface IP value in the Corporate IP field
-
Input the Sophos appliance's local subnet into the Corporate Subnet field.
-
Complete any other required fields. Then, at the top of the page, click Save Changes.
Good to know 
-
Click the below thumbnails to view example configurations that our Support team has confirmed to work with Sophos appliances.
-
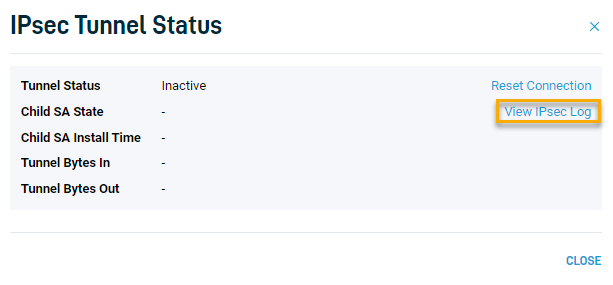
You can view the IPSec logs from your Secure Edge dashboard at Corporate Tunnel > More info > View IPSec Log.